#muslim Scientists
Explore tagged Tumblr posts
Text
Sorry for the lack of content y'all, it seems I've...
Fallen out of the Trolls fandom bit by bit. (GASP).
I know, shocking, but it is what it is.
Make no mistake, the Techno!Branch fic is still ongoing, it's just... gonna be slow from here on out. Sorry if you were expecting something big from it ><
There's a chance I'll start rambling/drawing stuff from different media, depending on how motivated I am. Just getting it out here.
But yeah, basically that's all I have to say, sorry if I disappointed anyone reading.
I'ma just say this to whoever may be reading this, but Happy Eid Mubarak to those who celebrate it! Minal Aidin Wal Faizin! ^^
#yeah im a muslim#if i start getting hate comments u bet ill post them here lol#i got nothing to do here so#lol#techno!branch au#trolls#btw the fandom im currently in is#honkai star rail#persona#a bit of fire emblem#and megaman#yknow i might just post fanart and ramblings of them in tbe future#so beware my mad scientist era lol
14 notes
·
View notes
Text
MOUNTAIN AS PEGS? Yes, it is!
Scientists & Geologists believe that mountains stabilize the earth's crust. If a small building needs a base called a foundation to make the structure stable on the earth, then they declared that mountains function like a peg upon the earth.
1) According to Dr. Frank Press, in his book ‘Earth’ he says “……..the mountains play an important role in stabilizing the crust of the earth……”.
2) “Andre Cailleux and J. Moody Stuart, Anatomy of the Earth (McGraw-Hill Companies: 1968), Pg 220.), states that “….. Mountains, like pegs, have deep roots embedded in the ground…”
3) According to Professor Siaveda, a world-renowned underwater geologist, “….by fixing the Earth's crust they prevent any sliding over the magma layer or amongst the layers themselves. In short, mountains can be compared to nails holding strips of wood together. The fixing effect of mountains is known as isostasy in scientific literature….”
4) G.B. Airy in 1855 suggested that mountains have a deep root of lower-density rock which the plains lack. Four years after Airy published his work, J.H Pratt offered an alternative hypothesis... By this hypothesis rock columns below mountains must have a lower density, because of their greater length, than shorter rock columns beneath plains. Both Airy and Pratt's hypotheses imply that surface irregularities are balanced by differences in the density of rocks below the major features (mountains & plains) of the crust. This state of BALANCE is described as the concept of ISOSTASY.
Thus Geology proved that mountains are like pegs.
5. Surprisingly, this truth was revealed by Allah in the 6th century. Quran declares that Allah has placed upon the earth's surface mountains firm (21:31, 16:15, 13:3, 79:32,15:19, 88:19) as the pegs (78:6-7) so that the earth should not shake (16:19, 21:31). In the second two stages during the creation of Earth, Allah placed upon the surface of the Earth firmly set mountains, He placed on the earth firm mountains, tall mountain (77:20) as pegs (78:6) lest it should shake with its inhabitants. Quran is so clear in this regard.

#quran#muslim#islam#allahﷻ#geology#mountains#mountain as pegs#scientist#earth science#scientists#scientific truths#geologist
20 notes
·
View notes
Text
I don't think a self cooling reactor means much if the whole reactor gets wiped out - which is what actually happened with Fukushima. All that saves is the active fuel rods. What about the rest of the process of a nuclear reactor, like disposal of wastewater & spent fuel rods? Are the Chinese govt actually proposing to share this technology, cause they never have before. So as much as this sounds amazing, I'm real skeptical.
#let's not jump for joy when this is coming from Chinese scientists in Xi run China#this is the same country killing their muslims#and native people who are against their president
0 notes
Text
What do you do on a 17-hour plane ride? You play a writing game with your girlfriend, then get obsessed about the characters you made and create a whole story.
At least, that's what I did. And now we're here... with a full-fledged short story.
Go check it out!
#fantasy#adventure#lgbtq#magic#writing#wattpad#new adult#science#maori#muslim#jack#anna#trish#magic mountain#short story#autism#scientists#own writing#international students#it was meant to be a game#now it's a full story
1 note
·
View note
Text
"I wanna see more Ramadhan + Eid art of Sumeru characters" -> "I should make such art myself" -> "Why do I always get these ideas when Ramadhan is almost over instead of like preparing for it a month or so before"
#specifically hthm and nari bcs they're named after irl muslim scientists but i think anyone is fair game#(except for dhya bcs her namesake historically fought against a muslim invasion so i think that might be disrespectful to her)#hopefully i can find other artists who'll do this too but for now.. i'll assume i have to cook for myself
0 notes
Text
KATIP CELEBI
KÂTİP ÇELEBİ (1609-1657): He was born in February 1609 in Istanbul. Information about his life is based on autobiographical works he wrote. His real name is Mustafa, his father's name is Abdullah. He became famous as Kâtib Çelebi among scholars, Hacı Halîfe among the members of Dîvân-ı Hümâyun, and Hacı Kalfa in the Western world. He was brought up from his father, Enderun, and was apprenticed with a task related to armed forces, he participated in the councils of the scholars and sheikhs of the period and showed great interest in science . When Kâtib Çelebi was five years old, he received the first religious information from Asa Halîfe al-Kırîmî, whom his father hired privately, and partially memorized the Quran. Later, he took grammar lessons from İlyas Hoca and writing lessons from Böğrü Ahmed Çelebi . When Kâtib Çelebi was fourteen years old, his father gave him 14 dirhams of pocket money from his salary and took him with him.
Thus, he entered the Anatolian Accounting Office, one of the items of Dîvân-ı Hümâyun , and learned the rules of account, power and politics here. He lost his father in August 1626 and his uncle a month later in Nusaybin. He stayed in Diyarbekir for a while. He was appointed to Süvari Quran by one of his father's friends, Mehmed Halîfe . When he returned to Istanbul, he continued the lessons of Kadızâde Mehmed Efendi. He participated in the Hamadan and Baghdad expeditions under Hüsrev Pasha's entourage. In his works Cihannümâ and Fezleke , he described his observations about cities and destinations such as Gülânber Castle, Hasanâbâd, Hamadan, Bîsütûn, which they visited or conquered during these expeditions . He died on the morning of October 6, 1657 and was buried in the cemetery around Zeyrek Mosque. THE LITERARY PERSONALITY OF THE CIPY CELEBI: His devotion to science and learning was after the Revan Campaign in 1635. Kâtib Çelebi, who explained his observations of this expedition in great detail, gave his later life almost entirely to scientific studies.
He invested a small legacy left to him in books. He started to write the names of the books he saw in secondhand shops while in Aleppo. Kâtib Çelebi, who liked to read works of history, saints and faithfulness, had read many such books until 1636 . Kâtib Çelebi, who has been dealing with science day and night for ten years, sometimes devotes himself to a book , forgets everything, a candle lights up in his room until the sun rises, and he never felt tired from it. On the occasion of the 1645 Crete expedition, he was also interested in mapping. Meanwhile, he left the civil service when he quarreled with the chief caliph over the staff issue . Kâtib Çelebi, who taught his son on various subjects besides other students, read medical books in order to learn the ways of healing during his illness, and also studied the esma and havas books in search of spiritual cures. for he was sure of the healing effects of prayers made with a clean heart. He translated some works from Latin to Turkish with the help of the Muslim French-born Mehmed İhlâsî . THE WORKS OF KÂTİP ÇELEBİ:
The most important works of Kâtip Çelebi,
To read more visit my blog
0 notes
Text
प्रिंटिंग बुक के फतवे ने कैसे इस्लामी दुनिया को मगरबी तरक्की से 300 साल पीछे पहुँचा दिया; मुहम्मद आदिल
मुहम्मद आदिल, 15 अप्रेल 2023, नई दिल्ली, एक फतवा आया और दुनिया की सबसे बड़ी हुकूमत तरक्की की दौड मे मगरीबी दुनिया से पिछड़ गयी, और इस एक कारण से हकूमत के ज्वाल का कारण बना, इस एक फतवे ने दुनिया के 3 महादीपो पर फेली उस दौर की सबसे बड़ी हुकूमत सल्तनत ए उस्मानिया को टुकड़े टुकड़े कर दिया मगर मुसलमान फिर भी सोता रहा, ये वो दीन का पेरोकर था जिस की पहली वही है इकरा (पढ़ो) वो कौम ही जहालत के अंधेरो में गुम…

View On WordPress
0 notes
Text
Forcing your computer to rat you out

Powerful people imprisoned by the cluelessness of their own isolation, locked up with their own motivated reasoning: “It’s impossible to get a CEO to understand something when his quarterly earnings call depends on him not understanding it.”
Take Mark Zuckerberg. Zuckerberg insists that anyone who wanted to use a pseudonym online is “two-faced,” engaged in dishonest social behavior. The Zuckerberg Doctrine claims that forcing people to use their own names is a way to ensure civility. This is an idea so radioactively wrong, it can be spotted from orbit.
From the very beginning, social scientists (both inside and outside Facebook) told Zuckerberg that he was wrong. People have lots of reasons to hide their identities online, both good and bad, but a Real Names Policy affects different people differently:
https://memex.craphound.com/2018/01/22/social-scientists-have-warned-zuck-all-along-that-the-facebook-theory-of-interaction-would-make-people-angry-and-miserable/
For marginalized and at-risk people, there are plenty of reasons to want to have more than one online identity — say, because you are a #MeToo whistleblower hoping that Harvey Weinstein won’t sic his ex-Mossad mercenaries on you:
https://www.newyorker.com/news/news-desk/harvey-weinsteins-army-of-spies
Or maybe you’re a Rohingya Muslim hoping to avoid the genocidal attentions of the troll army that used Facebook to organize — under their real, legal names — to rape and murder you and everyone you love:
https://www.amnesty.org/en/latest/news/2022/09/myanmar-facebooks-systems-promoted-violence-against-rohingya-meta-owes-reparations-new-report/
But even if no one is looking to destroy your life or kill you and your family, there are plenty of good reasons to present different facets of your identity to different people. No one talks to their lover, their boss and their toddler in exactly the same way, or reveals the same facts about their lives to those people. Maintaining different facets to your identity is normal and healthy — and the opposite, presenting the same face to everyone in your life, is a wildly terrible way to live.
None of this is controversial among social scientists, nor is it hard to grasp. But Zuckerberg stubbornly stuck to this anonymity-breeds-incivility doctrine, even as dictators used the fact that Facebook forced dissidents to use their real names to retain power through the threat (and reality) of arrest and torture:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Why did Zuck cling to this dangerous and obvious fallacy? Because the more he could collapse your identity into one unitary whole, the better he could target you with ads. Truly, it is impossible to get a billionaire to understand something when his mega-yacht depends on his not understanding it.
This motivated reasoning ripples through all of Silicon Valley’s top brass, producing what Anil Dash calls “VC QAnon,” the collection of conspiratorial, debunked and absurd beliefs embraced by powerful people who hold the digital lives of billions of us in their quivering grasp:
https://www.anildash.com/2023/07/07/vc-qanon/
These fallacy-ridden autocrats like to disguise their demands as observations, as though wanting something to be true was the same as making it true. Think of when Eric Schmidt — then the CEO of Google — dismissed online privacy concerns, stating “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place”:
https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy
Schmidt was echoing the sentiments of his old co-conspirator, Sun Microsystems CEO Scott McNealy: “You have zero privacy anyway. Get over it”:
https://www.wired.com/1999/01/sun-on-privacy-get-over-it/
Both men knew better. Schmidt, in particular, is very jealous of his own privacy. When Cnet reporters used Google to uncover and publish public (but intimate and personal) facts about Schmidt, Schmidt ordered Google PR to ignore all future requests for comment from Cnet reporters:
https://www.cnet.com/tech/tech-industry/how-cnet-got-banned-by-google/
(Like everything else he does, Elon Musk’s policy of responding to media questions about Twitter with a poop emoji is just him copying things other people thought up, making them worse, and taking credit for them:)
https://www.theverge.com/23815634/tesla-elon-musk-origin-founder-twitter-land-of-the-giants
Schmidt’s actions do not reflect an attitude of “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Rather, they are the normal response that we all have to getting doxed.
When Schmidt and McNealy and Zuck tell us that we don’t have privacy, or we don’t want privacy, or that privacy is bad for us, they’re disguising a demand as an observation. “Privacy is dead” actually means, “When privacy is dead, I will be richer than you can imagine, so stop trying to save it, goddamnit.”
We are all prone to believing our own bullshit, but when a tech baron gets high on his own supply, his mental contortions have broad implications for all of us. A couple years after Schmidt’s anti-privacy manifesto, Google launched Google Plus, a social network where everyone was required to use their “real name.”
This decision — justified as a means of ensuring civility and a transparent ruse to improve ad targeting — kicked off the Nym Wars:
https://epeus.blogspot.com/2011/08/google-plus-must-stop-this-identity.html
One of the best documents to come out of that ugly conflict is “Falsehoods Programmers Believe About Names,” a profound and surprising enumeration of all the ways that the experiences of tech bros in Silicon Valley are the real edge-cases, unreflective of the reality of billions of their users:
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
This, in turn, spawned a whole genre of programmer-fallacy catalogs, falsehoods programmers believe about time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families:
https://github.com/kdeldycke/awesome-falsehood
But humility is in short supply in tech. It’s impossible to get a programmer to understand something when their boss requires them not to understand it. A programmer will happily insist that ordering you to remove your “mask” is for your own good — and not even notice that they’re taking your skin off with it.
There are so many ways that tech executives could improve their profits if only we would abandon our stubborn attachment to being so goddamned complicated. Think of Netflix and its anti-passsword-sharing holy war, which is really a demand that we redefine “family” to be legible and profitable for Netflix:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
But despite the entreaties of tech companies to collapse our identities, our families, and our online lives into streamlined, computably hard-edged shapes that fit neatly into their database structures, we continue to live fuzzy, complicated lives that only glancingly resemble those of the executives seeking to shape them.
Now, the rich, powerful people making these demands don’t plan on being constrained by them. They are conservatives, in the tradition of #FrankWilhoit, believers in a system of “in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect”:
https://crookedtimber.org/2018/03/21/liberals-against-progressives/#comment-729288
As with Schmidt’s desire to spy on you from asshole to appetite for his own personal gain, and his violent aversion to having his own personal life made public, the tech millionaires and billionaires who made their fortune from the flexibility of general purpose computers would like to end that flexibility. They insist that the time for general purpose computers has passed, and that today, “consumers” crave the simplicity of appliances:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
It is in the War On General Purpose Computing that we find the cheapest and flimsiest rhetoric. Companies like Apple — and their apologists — insist that no one wants to use third-party app stores, or seek out independent repair depots — and then spend millions to make sure that it’s illegal to jailbreak your phone or get it fixed outside of their own official channel:
https://doctorow.medium.com/apples-cement-overshoes-329856288d13
The cognitive dissonance of “no one wants this,” and “we must make it illegal to get this” is powerful, but the motivated reasoning is more powerful still. It is impossible to get Tim Cook to understand something when his $49 million paycheck depends on him not understanding it.
The War on General Purpose Computing has been underway for decades. Computers, like the people who use them, stubbornly insist on being reality-based, and the reality of computers is that they are general purpose. Every computer is a Turing complete, universal Von Neumann machine, which means that it can run every valid program. There is no way to get a computer to be almost Turing Complete, only capable of running programs that don’t upset your shareholders’ fragile emotional state.
There is no such thing as a printer that will only run the “reject third-party ink” program. There is no such thing as a phone that will only run the “reject third-party apps” program. There are only laws, like the Section 1201 of the Digital Millennium Copyright Act, that make writing and distributing those programs a felony punishable by a five-year prison sentence and a $500,000 fine (for a first offense).
That is to say, the War On General Purpose Computing is only incidentally a technical fight: it is primarily a legal fight. When Apple says, “You can’t install a third party app store on your phone,” what they means is, “it’s illegal to install that third party app store.” It’s not a technical countermeasure that stands between you and technological self-determination, it’s a legal doctrine we can call “felony contempt of business model”:
https://locusmag.com/2020/09/cory-doctorow-ip/
But the mighty US government will not step in to protect a company’s business model unless it at least gestures towards the technical. To invoke DMCA 1201, a company must first add the thinnest skin of digital rights management to their product. Since 1201 makes removing DRM illegal, a company can use this molecule-thick scrim of DRM to felonize any activity that the DRM prevents.
More than 20 years ago, technologists started to tinker with ways to combine the legal and technical to tame the wild general purpose computer. Starting with Microsoft’s Palladium project, they theorized a new “Secure Computing” model for allowing companies to reach into your computer long after you had paid for it and brought it home, in order to discipline you for using it in ways that undermined its shareholders’ interest.
Secure Computing began with the idea of shipping every computer with two CPUs. The first one was the normal CPU, the one you interacted with when you booted it up, loaded your OS, and ran programs. The second CPU would be a Trusted Platform Module, a brute-simple system-on-a-chip designed to be off-limits to modification, even by its owner (that is, you).
The TPM would ship with a limited suite of simple programs it could run, each thoroughly audited for bugs, as well as secret cryptographic signing keys that you were not permitted to extract. The original plan called for some truly exotic physical security measures for that TPM, like an acid-filled cavity that would melt the chip if you tried to decap it or run it through an electron-tunneling microscope:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
This second computer represented a crack in the otherwise perfectly smooth wall of a computer’s general purposeness; and Trusted Computing proposed to hammer a piton into that crack and use it to anchor a whole superstructure that could observe — and limited — the activity of your computer.
This would start with observation: the TPM would observe every step of your computer’s boot sequence, creating cryptographic hashes of each block of code as it loaded and executed. Each stage of the boot-up could be compared to “known good” versions of those programs. If your computer did something unexpected, the TPM could halt it in its tracks, blocking the boot cycle.
What kind of unexpected things do computers do during their boot cycle? Well, if your computer is infected with malware, it might load poisoned versions of its operating system. Once your OS is poisoned, it’s very hard to detect its malicious conduct, since normal antivirus programs rely on the OS to faithfully report what your computer is doing. When the AV program asks the OS to tell it which programs are running, or which files are on the drive, it has no choice but to trust the OS’s response. When the OS is compromised, it can feed a stream of lies to users’ programs, assuring these apps that everything is fine.
That’s a very beneficial use for a TPM, but there’s a sinister flipside: the TPM can also watch your boot sequence to make sure that there aren’t beneficial modifications present in your operating system. If you modify your OS to let you do things the manufacturer wants to prevent — like loading apps from a third-party app-store — the TPM can spot this and block it.
Now, these beneficial and sinister uses can be teased apart. When the Palladium team first presented its research, my colleague Seth Schoen proposed an “owner override”: a modification of Trusted Computing that would let the computer’s owner override the TPM:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
This override would introduce its own risks, of course. A user who was tricked into overriding the TPM might expose themselves to malicious software, which could harm that user, as well as attacking other computers on the user’s network and the other users whose data were on the compromised computer’s drive.
But an override would also provide serious benefits: it would rule out the monopolistic abuse of a TPM to force users to run malicious code that the manufacturer insisted on — code that prevented the user from doing things that benefited the user, even if it harmed the manufacturer’s shareholders. For example, with owner override, Microsoft couldn’t force you to use its official MS Office programs rather than third-party compatible programs like Apple’s iWork or Google Docs or LibreOffice.
Owner override also completely changed the calculus for another, even more dangerous part of Trusted Computing: remote attestation.
Remote Attestation is a way for third parties to request a reliable, cryptographically secured assurances about which operating system and programs your computer is running. In Remote Attestation, the TPM in your computer observes every stage of your computer’s boot, gathers information about all the programs you’re running, and cryptographically signs them, using the signing keys the manufacturer installed during fabrication.
You can send this “attestation” to other people on the internet. If they trust that your computer’s TPM is truly secure, then they know that you have sent them a true picture of your computer’s working (the actual protocol is a little more complicated and involves the remote party sending you a random number to cryptographically hash with the attestation, to prevent out-of-date attestations).
Now, this is also potentially beneficial. If you want to make sure that your technologically unsophisticated friend is running an uncompromised computer before you transmit sensitive data to it, you can ask them for an attestation that will tell you whether they’ve been infected with malware.
But it’s also potentially very sinister. Your government can require all the computers in its borders to send a daily attestation to confirm that you’re still running the mandatory spyware. Your abusive spouse — or abusive boss — can do the same for their own disciplinary technologies. Such a tool could prevent you from connecting to a service using a VPN, and make it impossible to use Tor Browser to protect your privacy when interacting with someone who wishes you harm.
The thing is, it’s completely normal and good for computers to lie to other computers on behalf of their owners. Like, if your IoT ebike’s manufacturer goes out of business and all their bikes get bricked because they can no longer talk to their servers, you can run an app that tricks the bike into thinking that it’s still talking to the mothership:
https://nltimes.nl/2023/07/15/alternative-app-can-unlock-vanmoof-bikes-popular-amid-bankruptcy-fears
Or if you’re connecting to a webserver that tries to track you by fingerprinting you based on your computer’s RAM, screen size, fonts, etc, you can order your browser to send random data about this stuff:
https://jshelter.org/fingerprinting/
Or if you’re connecting to a site that wants to track you and nonconsensually cram ads into your eyeballs, you can run an adblocker that doesn’t show you the ads, but tells the site that it did:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Owner override leaves some of the beneficial uses of remote attestation intact. If you’re asking a friend to remotely confirm that your computer is secure, you’re not going to use an override to send them bad data about about your computer’s configuration.
And owner override also sweeps all of the malicious uses of remote attestation off the board. With owner override, you can tell any lie about your computer to a webserver, a site, your boss, your abusive spouse, or your government, and they can’t spot the lie.
But owner override also eliminates some beneficial uses of remote attestation. For example, owner override rules out remote attestation as a way for strangers to play multiplayer video games while confirming that none of them are using cheat programs (like aimhack). It also means that you can’t use remote attestation to verify the configuration of a cloud server you’re renting in order to assure yourself that it’s not stealing your data or serving malware to your users.
This is a tradeoff, and it’s a tradeoff that’s similar to lots of other tradeoffs we make online, between the freedom to do something good and the freedom to do something bad. Participating anonymously, contributing to free software, distributing penetration testing tools, or providing a speech platform that’s open to the public all represent the same tradeoff.
We have lots of experience with making the tradeoff in favor of restrictions rather than freedom: powerful bad actors are happy to attach their names to their cruel speech and incitement to violence. Their victims are silenced for fear of that retaliation.
When we tell security researchers they can’t disclose defects in software without the manufacturer’s permission, the manufacturers use this as a club to silence their critics, not as a way to ensure orderly updates.
When we let corporations decide who is allowed to speak, they act with a mixture of carelessness and self-interest, becoming off-the-books deputies of authoritarian regimes and corrupt, powerful elites.
Alas, we made the wrong tradeoff with Trusted Computing. For the past twenty years, Trusted Computing has been creeping into our devices, albeit in somewhat denatured form. The original vision of acid-filled secondary processors has been replaced with less exotic (and expensive) alternatives, like “secure enclaves.” With a secure enclave, the manufacturer saves on the expense of installing a whole second computer, and instead, they draw a notional rectangle around a region of your computer’s main chip and try really hard to make sure that it can only perform a very constrained set of tasks.
This gives us the worst of all worlds. When secure enclaves are compromised, we not only lose the benefit of cryptographic certainty, knowing for sure that our computers are only booting up trusted, unalterted versions of the OS, but those compromised enclaves run malicious software that is essentially impossible to detect or remove:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
But while Trusted Computing has wormed its way into boot-restrictions — preventing you from jailbreaking your computer so it will run the OS and apps of your choosing — there’s been very little work on remote attestation…until now.
Web Environment Integrity is Google’s proposal to integrate remote attestation into everyday web-browsing. The idea is to allow web-servers to verify what OS, extensions, browser, and add-ons your computer is using before the server will communicate with you:
https://github.com/RupertBenWiser/Web-Environment-Integrity/blob/main/explainer.md
Even by the thin standards of the remote attestation imaginaries, there are precious few beneficial uses for this. The googlers behind the proposal have a couple of laughable suggestions, like, maybe if ad-supported sites can comprehensively refuse to serve ad-blocking browsers, they will invest the extra profits in making things you like. Or: letting websites block scriptable browsers will make it harder for bad people to auto-post fake reviews and comments, giving users more assurances about the products they buy.
But foundationally, WEI is about compelling you to disclose true facts about yourself to people who you want to keep those facts from. It is a Real Names Policy for your browser. Google wants to add a new capability to the internet: the ability of people who have the power to force you to tell them things to know for sure that you’re not lying.
The fact that the authors assume this will be beneficial is just another “falsehood programmers believe”: there is no good reason to hide the truth from other people. Squint a little and we’re back to McNealy’s “Privacy is dead, get over it.” Or Schmidt’s “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
And like those men, the programmers behind this harebrained scheme don’t imagine that it will ever apply to them. As Chris Palmer — who worked on Chromium — points out, this is not compatible with normal developer tools or debuggers, which are “incalculably valuable and not really negotiable”:
https://groups.google.com/a/chromium.org/g/blink-dev/c/Ux5h_kGO22g/m/5Lt5cnkLCwAJ
This proposal is still obscure in the mainstream, but in tech circles, it has precipitated a flood of righteous fury:
https://arstechnica.com/gadgets/2023/07/googles-web-integrity-api-sounds-like-drm-for-the-web/
As I wrote last week, giving manufacturers the power to decide how your computer is configured, overriding your own choices, is a bad tradeoff — the worst tradeoff, a greased slide into terminal enshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is how you get Unauthorized Bread:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
All of which leads to the question: what now? What should be done about WEI and remote attestation?
Let me start by saying: I don’t think it should be illegal for programmers to design and release these tools. Code is speech, and we can’t understand how this stuff works if we can’t study it.
But programmers shouldn’t deploy it in production code, in the same way that programmers should be allowed to make pen-testing tools, but shouldn’t use them to attack production systems and harm their users. Programmers who do this should be criticized and excluded from the society of their ethical, user-respecting peers.
Corporations that use remote attestation should face legal restrictions: privacy law should prevent the use of remote attestation to compel the production of true facts about users or the exclusion of users who refuse to produce those facts. Unfair competition law should prevent companies from using remote attestation to block interoperability or tie their products to related products and services.
Finally, we must withdraw the laws that prevent users and programmers from overriding TPMs, secure enclaves and remote attestations. You should have the right to study and modify your computer to produce false attestations, or run any code of your choosing. Felony contempt of business model is an outrage. We should alter or strike down DMCA 1201, the Computer Fraud and Abuse Act, and other laws (like contract law’s “tortious interference”) that stand between you and “sole and despotic dominion” over your own computer. All of that applies not just to users who want to reconfigure their own computers, but also toolsmiths who want to help them do so, by offering information, code, products or services to jailbreak and alter your devices.
Tech giants will squeal at this, insisting that they serve your interests when they prevent rivals from opening up their products. After all, those rivals might be bad guys who want to hurt you. That’s 100% true. What is likewise true is that no tech giant will defend you from its own bad impulses, and if you can’t alter your device, you are powerless to stop them:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Companies should be stopped from harming you, but the right place to decide whether a business is doing something nefarious isn’t in the boardroom of that company’s chief competitor: it’s in the halls of democratically accountable governments:
https://www.eff.org/wp/interoperability-and-privacy
So how do we get there? Well, that’s another matter. In my next book, The Internet Con: How to Seize the Means of Computation (Verso Books, Sept 5), I lay out a detailed program, describing which policies will disenshittify the internet, and how to get those policies:
https://www.versobooks.com/products/3035-the-internet-con
Predictably, there are challenges getting this kind of book out into the world via our concentrated tech sector. Amazon refuses to carry the audio edition on its monopoly audiobook platform, Audible, unless it is locked to Amazon forever with mandatory DRM. That’s left me self-financing my own DRM-free audio edition, which is currently available for pre-order via this Kickstarter:
http://seizethemeansofcomputation.org

I’m kickstarting the audiobook for “The Internet Con: How To Seize the Means of Computation,” a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It’s a DRM-free book, which means Audible won’t carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation

If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai

[Image ID: An anatomical drawing of a flayed human head; it has been altered to give it a wide-stretched mouth revealing a gadget nestled in the back of the figure's throat, connected by a probe whose two coiled wires stretch to an old fashioned electronic box. The head's eyes have been replaced by the red, menacing eye of HAL 9000 from Stanley Kubrick's '2001: A Space Odyssey.' Behind the head is a code waterfall effect as seen in the credits of the Wachowskis' 'The Matrix.']

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#chaffing#spoofing#remote attestation#rene descartes#adversarial interoperability#war on general purpose computing#canvas attacks#vpns#compelled speech#onion routing#owner override#stalkerware#ngscb#palladium#trusted computing#secure enclaves#tor#interop#net neutrality#taking the fifth#right to remain silent#real names policy#the zuckerberg doctrine#none of your business#the right to lie#right to repair#bossware#spyware#wei web environment integrity
2K notes
·
View notes
Text
There is a great engine beneath the North American continent that drives people to insanity and spits out new religions on a regular basis. Maybe the lingering tectonic energies of Yellowstone, worrying at us just below our conscious awareness and driving us to a quiet, gibbering fear like rats scurrying about just before an earthquake. Maybe a kink in the Earth's magnetic field that affects our brains in some way. Maybe just the shock of agoraphobia, of wandering out into wide open spaces and going mad beneath the vast and starry sky.
Over in Europe they spent a thousand years fighting wars and piling up the dead in hills of gore, all to determine trivialities like the true nature of the Eucharist, or who really had the authority to appoint bishops. Muslim kings killed each other by the score over who was the rightful successor of the Prophet. The scholar-officials of China carefully composed the orthodox interpretations of the rites and laws, and then the Emperor had everybody who disagreed beheaded. Oh, there were heretics all right, but the stakes within each tradition were low--is Christ of one substance or two? Which hadith are valid? Is there a true and eternal self, or no?
In the United States, though, people sought the edge of civilization, declared that here lay the Frontier. They stepped beyond it, and then they went stark raving mad. They declared the ghost of Ben Franklin was telling them how to build a mechanical Jesus. They said an evil scientist created white people as soulless devils on the Greek island of Patmos. That all our anxieties are caused by the restless ghosts of alien political prisoners, executed by volcano. That God was once a man, and we too might become gods someday, as long as we remembered that coffee-drinking was a sin.
And it's no coincidence that every major American religious movement seems to be founded by an obvious con man. I think that's the secret to being a prophet. You have to learn to lie. To lie so nakedly and so intensely that the things you are lying about appear before your very eyes, become tangible to you and to everyone who believes. Ordinary, simple, sincere faith will not do. You must learn to lie with such intensity that you can change the world.
733 notes
·
View notes
Text
What The Fuck is Wrong with You?
Elect Biden and shut the fuck up about his age.
Donald J Trump is arguably the most ignorant, disgusting, demented man that anyone in America can name. Why are Democrats, news pundits and internet morons continuing to talk about Biden being old?
Donald Trump tried to overthrow the government of the United States of America and lost over 60 lawsuits to that effect. He incited and supported an insurrection that saw Americans attack the Capitol and try to capture or kill American lawmakers.
Who the fuck cares if Biden is old?
Donald J Trump named three Supreme Court Justices who ended Roe v Wade and have now rendered the Separation of Powers and check and balances in the US Constitution as "null and void."
Biden is just 3 years older than Trump, and who cares?
Donald Trump goes on insane, meandering, half-baked rants at political rallies, slurring his words, unable to complete sentences, losing track of his thoughts, and calling for Americans to be hurt, have their rights taken away and worse. He treats everyone around him, including other Republicans, like trash.
But Biden is old.
Donald Trump pretended that COVID was a hoax, suggested the American people ingest bleach to fight it, and smeared the leading scientists battling COVID, which resulted in about a million deaths in the United States in a year.
But Joe Biden is pretty old.
Donald Trump was accused of rape by over 20 women, found guilty of sexual assault in 2024 and made lurid comments about his own daughter. He also cheated on all three of his wives, including his latest wife while she was pregnant. Then he tried to cover it up by paying hush money to a porn star.
Biden is an old guy.
Donald Trump banned Muslims from America, put thousands of people in cages at the border and tried to get the Ukrainian president to lie about Joe Biden.
But Joe Biden isn't a youngin anymore.
Trump said African nations were "shithole countries" and said white supremacists were "very fine people." Trump said immigrants were taking "Black jobs". He also ignored the hurricane catastrophe in Puerto Rico, which took 3000 lives.
But Biden is old.
Trump's family foundation was found to have ripped off charities, he's banned from doing business in New York, and his daughter and son-in-law received $2 billion from the Saudis at the end of his presidency. He's bankrupted or failed in every business he's ever had, from Trump Steaks to Trump Air to Trump University to all the casinos.
But hey, Biden is old.
Trump did a deal with Afghanistan to let the Taliban out of prison so they could (and did) take over the country. He's sided with Putin against NATO. He said nothing about the Saudis killing a journalist. Donald Trump eased restrictions on loan sharks, exploded the deficit and made friends with North Korea. He told over 3000 lies.
But old Joe is old.
Biden is old.
Donald Trump is easily the worst human being anyone has ever encountered, and all anyone can talk about is how old Biden is. What the fuck is wrong with you?

295 notes
·
View notes
Text
If you are against religion, you can't just be against Christianity. If you hate religion as a concept and as a practice, that means you have to hate *all* religion, including the marginalized ones. If you're antithiest, you're not just antichristian. Your Anti Islam, Anti Judaism, you have to be against all religions, even "the good kind."
I am against *all* religion because it is a harmful practice that indoctrinates people into stupidity and blissful ignorance. There is no such thing as a Christian Scientist. There is no such thing as a Muslim Feminist. There is no such thing as a good religion. The sooner we realize that, the better.
With that being said, I'm not gonna harass religious people. Just know that I am against your beliefs. If that's enough for you to block me, so be it.
70 notes
·
View notes
Text
Mountains act like a peg-Proved
There are two misinterpretations among certain classes of people who don't want to agree that (1) Allah spread the Earth with provisions. But that says Quran speaks that the earth is flat. Next... (2) They say mountains are a creation of turbulence upon the earth, that happened once upon a time and not at all functions as pegs.
Scientists and geologists already declared that a mountain acts like pegs whatever may be the mode of its creation. Arno Kleber in his book "Fundamentals of Geology", speaks that “Mountains are like a swimming iceberg, whose lower parts are below the water level. The heavier the mountains, the deeper the root" . Andre Cailleux and J. Moody Stuart, in their book "Anatomy of the Earth (McGraw-Hill Companies: 1968), Pg 220.), clearly declared that “…Mountains, like pegs, have deep roots embedded in the ground…" Further, Professor Siaveda, a world-renowned underwater geologist said the "... the mountains can be compared to nails holding strips of wood together and this fixing effect of mountains is known as isostasy in scientific literature… by fixing the Earth's crust they prevent any sliding over the magma layer or amongst the layers themselves.”
So the matter is clear and there should not be any disputes in this regard in the Quran when it declares mountains as pegs.
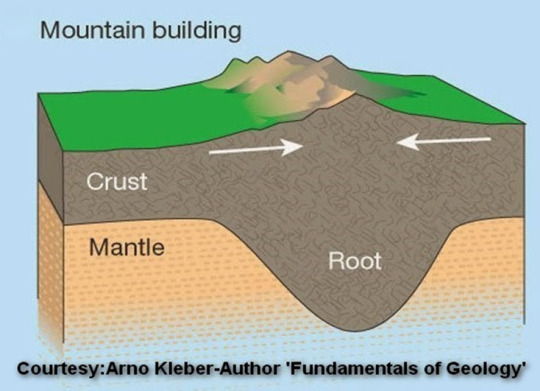
#quran#islam#muslim#allahﷻ#prophet muhammad#geology#mountains#geologists#earth science#science facts#mountain as pegs#scientists
11 notes
·
View notes
Note
do muslims consider people from nation of islam to be muslims?
The whole "Yakub is a scientist who created white people on the Greek island of Patmos" and the whole "mother ship" thing are an immediate disqualification from Islam, since it has no Qur'anic basis. This is not some Takfiri thing, it's just that, literally nothing about NOI is consistent with scripture.
69 notes
·
View notes
Text
Some good news to get you through
As someone super into history and current events, everything always sucks so I just want to make a little masterlist of some glimmers of hope. Will try to make multiple of these.
I shopped around for all of these, but this website and this website offers happy stories all in one place for those who don't have the time.
Colombia outlaws child marriage after 17-year campaign
Jordan Recognized as First in the World to Eradicate Leprosy
Norway, Paraguay, Antigua and Barbuda join the Global Alliance Against Hunger and Poverty
Orran Gala Raises $400,000 for Armenia’s Most Vulnerable
Hanover firefighter creates ‘Belize Heroes’ to donate lifesaving equipment to home country
Norway’s Kon-Tiki Museum returns artifacts to Chile’s remote Easter Island
Minneapolis man's murder conviction vacated after 16 years
Hiking group for Muslim women breaks barriers as hundreds flock to the outdoors
Scientists find a 35,000-year-old saber-toothed kitten in the Siberian permafrost
Tupelo Preschool Teacher Donates Organ to Student
Author Katherine Rundell donates royalties to climate charities in Trump protest
Pan-Mass Challenge Raises Record $75 Million for Dana-Farber Cancer Institute
Texas woodpecker no longer endangered after 54 years
Researchers discover 'lost' frog species in the Andes after over a century
More states are adopting laws to protect children of family vloggers
A 19-Year-Old Who Spent Her Childhood In Foster Care Was Finally Adopted By A Former Caseworker
Dolly Parton Gifts $4.5 Million to Nashville Public Library
New Mexico sees nearly 10% more first-year college students, bucking national trend
21-Year-Old Raising His 4 Siblings Since Their Mom Died Surprised With $40K and a New Car
Easy-fit prosthetics offer hope to thousands of Gaza amputees
UNM alumni hike tallest peaks in Ecuador to make prosthetic care more accessible
London charity helps young mums thrive
Italian charity sends 15 tonnes of humanitarian aid to Gaza via Cyprus
Climate report shows the largest annual drop in EU greenhouse gas emissions for decades
Washingtonians defend the Climate Commitment Act
Voters decide MN Lottery will keep funding environmental causes
Finnish fathers taking nearly double length of paternity leave since 2022 reform
Oysters reintroduced to Firth of Forth appear to be 'thriving'
German union says auto and engineering workers to get 5.5% wage rise
Seaweed farming brings hope to Kenyan villagers hit by climate change
Previously extinct Cape Water Lily restored at False Bay Nature Reserve
From landfill to limelight, Ghana waste entrepreneurs win Earthshot Prize
A derogatory term for Native women will be removed from place names across California
Texas Native Health expands facility to better serve the state's Indigenous community
Borneo’s ‘omen birds’ find a staunch guardian in Indigenous Dayak Iban elders
African cinema takes to global stage with diverse storytelling
Maori haka in NZ parliament to protest at bill to reinterpret founding treaty
Animal welfare group works to rescue lions, pets in Lebanon
Inside a Massachusetts studio showcasing the work of artists with disabilities
#mental health#positivity#self care#mental illness#self help#recovery#news#current events#politics#us politics#disability#disabled#neurodivergent#neurodiversity#autism#autistic#lgbt#lgbtq#art#indigenous#aesthetic#cute#body positivity#body positive#punk#positive reminders#positive vibes#self esteem#self worth#self improvement
27 notes
·
View notes
Text
Evliya Çelebi ottoman traveller

Even though those who know him call him 'the cheerleader', 'the master', he called himself the one he knew (hezar-familiar), the non-hypocritical (bi-riya), human friend. He has traveled a lot, has seen a lot, and the most beautiful is what he has seen. Who am I talking about: Evliya Çelebi. When we say traveler, Evliya Çelebi comes to mind first. He traveled from one end of the Ottoman Empire to the other with his travels. He went beyond the Ottoman borders, either in the nature of the pashas or as a government official. He made notes about the places he visited and made comparisons. He collected these near-death notes in the Book of Travels. He says that he was born in Istanbul on 25 March 1611 AD, 10 Hijri Muharram, 1020. “10 Muharrem” is an important day for Evliya Çelebi: the day of Ashura.
He gave the dates of the days he considered important, as "10 Muharram". He started his education in the primary school in his district and then continued in a madrasah. While he was a hafiz in Ayasofya Mosque in 1635, IV. He entered the palace with the admiration of Murat and received education for 5 years. Apart from Turkish, he learned Arabic, Persian, Greek and Latin. Evliya's life changes with the dream she saw on 10 Muharram 1040/19 August 1630 (another day of Ashura) . In his dream, in Ahi Çelebi Mosque, Hz. He saw Muhammad and his companions together. Hz. While kissing the hand of the Prophet, he would say "Intercession ya Rasulallah" and said "Travel or Resulallah". Hz. The Prophet also smiled and prayed, "Make travel and visit easy for this servant, O Lord." After that, he kisses the hand of the companions in the congregation and takes their prayers. Sa'd bin Ebu Vakkas from among the Companions advised him to write what he saw during the trip.
After the dream, Evliya Çelebi begins to explore Istanbul. He made his first trip out of Istanbul to Bursa in 1640. Bursa trip was
Read more visit my blog
0 notes
Text
मुस्लिम वैज्ञानिक, अल-बेरूनी: समय को 'क़ैद करने' की कोशिश करने वाले वैज्ञानिक, जिन्हें भारतीय सभ्यता में रुचि थी ।
22 मार्च 2023, नई दिल्ली, मुहम्मद आदिल, इस्लाम अपने उरूज से ही इल्म का गहवारा रहा है, इस्लाम ने दुनिया को अपने विजन से अनेक अविष्कार दिये है और दुनिया के तमाम विषयों के जनक वैज्ञानिक इस्लाम से तालुक रखते है, दुनिया की आला दर्जे की यूनिवर्सिटी आज भी अपने तकनीकी विभागों मे मुस्लिम वैज्ञानिकों की लिखी किताबो से पढ़ती है, मगर अफ़सोस की मुसलमानो ने अब पढ़ना कम कर दिया और अब अपने ज्वाल के खामोश तमाशाई…

View On WordPress
0 notes